Top 5 Web Application Firewall (WAF)

Businesses are increasingly using mobile and desktop web applications to boost staff productivity and give their customers a rewarding user experience. There is also a downside to this trend: as the number of applications increases, so does the number of cyberthreats. In a recent report on global threats to Internet security, Symantec pointed out that intruders mount attacks against websites by exploiting vulnerabilities of server web applications or vulnerabilities of the operating system hosting such applications.
Cybercriminals typically target various financial institutions: banks, insurance companies, online e-commerce platforms. Oftentimes a web application becomes the main entry point for a hacker. In this case the nature of the web resource itself is irrelevant. Nowadays, even a user who is not particularly knowledgeable in this field can attempt to hack a security system. After all, descriptions of the hacking technology and all the necessary tools for this are available on the web, which means they can be found using ordinary search engines.
Why WAF?

In the overwhelming majority of attacks on websites, intruders exploit vulnerabilities of applications. Moreover, even if the company has an antivirus and firewall installed, these tools are not very effective in fending off such threats. In the overwhelming majority of attacks on websites, attackers exploit vulnerabilities not of network infrastructure, but of applications.
High-quality protection calls for a different approach. It involves running in-depth analysis of packet data content and considering the structural features of the web application. A tool like this is Web Application Firewall (WAF) – a dedicated firewall designed to analyze data transmitted while accessing applications.
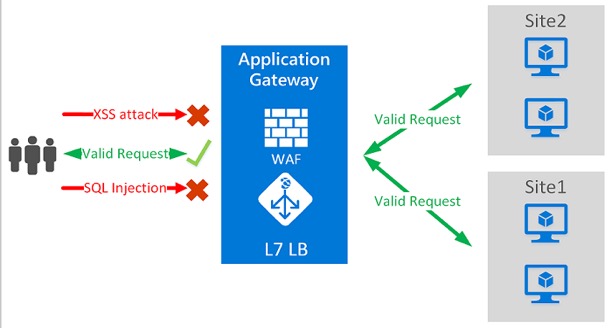
Web Application Firewall operating principle flowchart
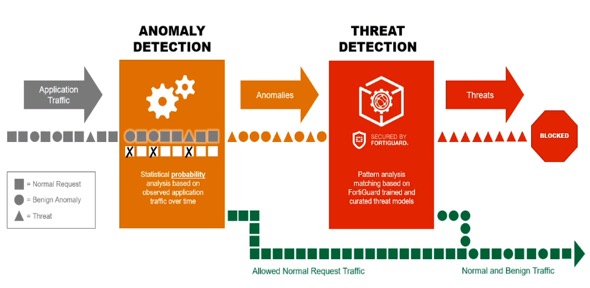
Signature. WAF with two-level machine learning technology
To detect a cyberattack, Web Application Firewall uses two key approaches: signature-based and behavioral. Integration of these two technologies can ensure a high level of protection, because hackers attacking websites can use so-called zero-day vulnerabilities that render the signature-based approach completely ineffective. Meanwhile, the behavioral approach involves constantly analyzing application performance works through a detailed analysis of network traffic and system logs. If major deviations are detected, the warning and protection system is triggered.
Incidentally, a gigantic number of false positive detections of various suspicious events is one of the drawbacks of a conventional firewall. This makes it very difficult to understand the actual degree of a threat on account of having to manually skim through multiple notifications. Meanwhile, Web Application Firewall automatically analyzes dozens and even hundreds of events and then displays information about the progress of the attack – from start to end.
Product selection criteria
Web Application Firewall products are currently in demand with companies of various sizes, so the majority of famous global vendors have already marketed their own product versions. Barracuda Networks Citrix, F5, Fortinet, and Imperva are among the best known players. Below is an overview of popular solutions on the market. More details about them are available in the WAF comparison table,
where you can compare all products across all parameters. We will try
to highlight their key properties and merits in our review.
Barracuda Web Application Firewall
Barracuda Web Application Firewall is an effective integrated system designed to ensure the security of web applications and sites. The product is a powerful deterrent against attackers who exploit vulnerabilities in protocols or applications for data theft, service disruption, or website defacing. It is noteworthy that the solution by Barracuda WAF has both an English and Russian-language interface.
Barracuda’s product provides protects against such attacks as SQL code injection, cross-site scripting (XSS), hacking of sessions, and buffer overflow. Barracuda WAF also prevents theft of information by monitoring all outgoing data for any leaks of sensitive information: bank account numbers, personal details of users, passwords, and so forth.
The system administrator can detect DoS and DDoS attacks in a timely manner owing to a dedicated function that monitors the data rate. A powerful built-in antivirus scans any data and files imported into the system for all kinds of malware.
Barracuda Web Application Firewall is fully compatible with most common authentication systems (Active Directory, eDirectory) that support LDAP RADIUS. It also has a two-factor identification feature: the system supports user authenticators and tokens (RSASecureID) to ensure reliable protection of client authentication.
Citrix NetScaler Application Firewall
NetScaler Web App Firewall by Citrix, a part of the integrated Citrix NetScaler solution, is one of the best-in-class Web Application Firewalls (WAF), which protects both websites and applications against various attacks, including threats at the application level and zero-day vulnerabilities.
The product is intended for the public sector, big and medium businesses. NetScaler Web App Firewall is supplied both as a virtual machine and as a hardware complex, and is also available as a cloud service.
NetScaler Application Firewall by Citrix protects against SQL injection attacks, XSS, modification of read-only (hidden) parameters, and other attacks. It comes with a data leak prevention function that prevents theft of credit card data and other confidential information, filters and blocks information being transmitted as needed.
To adapt NetScaler WAF to an evolving application, a web application protection profile is created, which covers all of the most common and dangerous threats by default. Over time, this profile is gradually updated and populated with data.
The bandwidth of Citrix Web Application Firewall ranges from 500 Mbps to 44 Gbps. Citrix WAF is offered as a standalone solution or is integrated into the Citrix ADC platform. According to NSS Labs, Citrix Web Application Firewall is one of the leaders in terms of the price / performance ratio among Web Application Firewalls.
For companies intending to migrate their applications and data to the cloud, Citrix Web App Firewall Security Service will come in handy. This product is simple to configure. The pay-as-you-grow model is also available at the time of purchase. This allows you to spend the exact amount that is needed for ongoing tasks, while scaling the product up or down as needed.
F5 Networks Silverline Web Application Firewall
A few years ago, F5 Networks brought to the market a cloud-powered service called Silverline Web Application Firewall (WAF) designed to repel attacks against web applications. This product is available by subscription.
Silverline WAF offers 24×7 support by security experts. First of all, such support enables companies to protect data and web applications. Second, it ensures compliance with industry-specific security standards, such as PCI DSS.
Silverline WAF protects applications against attacks based on SQL code injection, zero-day attacks, JSON attachments, OWASP Top Ten, etc. A key advantage of Silverline WAF is an automatic self-learning feature that uses iRules and iApps technologies for real-time reconfiguration to adapt to the specifics of new threats.
The product delivers operating cost savings by using the special resources of the F5 Networks Security Center for management of WAF policies. The integrated proactive monitoring feature by F5 Networks employs external specialist solutions to protect applications against new attacks. The solution generates reports on access gained through the customer portal.
Fortinet FortiWeb
The Fortinet FortiWeb web application firewall targets medium and large businesses as well as Internet service providers. The product is delivered as a hardware or virtual machine, as well as a cloud service. With support from the FortiGuard Labs security team, FortiWeb provides protection against the latest application vulnerabilities, bots, and suspicious URLs. Also, two threat detection mechanisms based on machine learning technology protect web applications against such complex cyber risks as SQL injection, cross-site scripting, buffer overflow, malicious cookie modifications, sources of threats and DoS attacks.
The FortiWeb threat detection function powered by behavioral analysis uses two levels of AI-based machine learning and statistical probabilities to detect anomalies and specific threats. Thanks to machine learning, FortiWeb can provide almost 100% accuracy of detection of threats to applications without using almost any resources. Owing to artificial intelligence, FortiWeb is an almost off-the-shelf WAF solution that runs according to the “set and forget” principle without sacrificing accuracy and reliability.
Fortinet is constantly working to detect new threats at its own analytical facility, FortiGuard Security Center. Owing to this approach, signatures, blacklists of sites and reputation bases are updated several times a day.
FortiWeb can provide temporary application patches until development teams deploy permanent vulnerability fixes. While it is usually recommended to permanently fix a known vulnerability, there are many cases when it is impossible or impractical, for example in the case of legacy or old applications that will soon be phased out.
Full compatibility of all Fortinet products allows scaling the system up or down quickly and easily. The high degree of automation of operations and the simplicity of their support reduces the number of human errors. This feature also allows downsizing the information security department staff.
Imperva SecureSphere Web Application Firewall
Imperva solutions are designed for the public sector as well as at large and medium businesses. The products are interesting in that they use several cybersecurity technologies at once: monitoring of protocols for abnormal behavior, dynamic profiling, signature-based analysis, and session tracking. Quality support is provided for all Imperva products. This product family is also known for its simple installation and configuration procedure.
The Imperva web application firewall consists of two primary modules:
SecureSphere Web Application Firewall – protection of web applications against cyber attacks
ThreatRadar – a reputation database
Effective protection is provided using mechanisms based on signatures of the free open-source intrusion prevention system called Snort, as well as its own SQL signatures generated by the ADC (Application Defense Center) research facility. In terms of fault tolerance, the product supports Active-Active and Active-Passive clustering.
SecureSphere WAF comes with a non-embeddable sniffer, transparent proxy server, and reverse proxy server, and offers excellent SSL support. In this way the product provides passive decryption of SSL, support of sessions established using client certificates, termination and determination (i.e., analysis of SSL traffic without termination). It is equally important that the solution contains hardware modules that accelerate SSL processing.
The product generates a reference security model using the method of classification of rules and application of detailed signatures (using firewall rules, creating signatures and processing protocol violations). To adapt WAF to an evolving application, the web application profile created in machine learning mode can be modified. It also offers the capability to configure the web application profile manually.
The product can be delivered as a virtual machine, a hardware complex, or as a cloud service. The maximum supported bandwidth of the older model is up to 10 Gbps. In addition to HTTP / HTTPS, it supports WebSockets, XMS, and JSON web standards.
The report generator available in SecureSphere WAF provides system administrators with reports aligned with the requirements of information security standards. It also allows generating customized reports (including scheduled reports) and exporting them to various formats.
Another important merit of SecureSphere WAF devices is the availability of the ThreatRadar service that provides almost instantaneous protection against attacks. ThreatRadar allows you to quickly block traffic from suspicious sources long before any harm can be done.
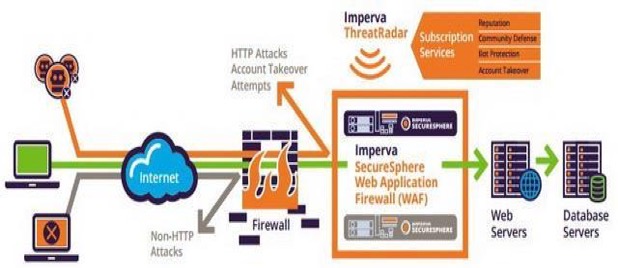
Summary
All products described above are market leaders and provide high-quality protection. However, to make sure that the configuration is correct, experts recommend running a so-called penetration test once the security system is up and running. It allows you test the actual level of security of the information system by imitating targeted attacks of various kinds.
--
Author: Oleg Pylypenko, for ROI4CIO
Author: Oleg Pylypenko, for ROI4CIO
*Article was previously published at Connection Cafe





Leave a Comment